This article will describe the use of conditional access and how traffic are being routed and expected to be coming from.
In order to enforce user's O365/Microsoft traffic to be only accepted from a certain location (Typically Public IP), "Named location" will be needed to define either "Countries location" or "IP ranges location".
https://www.inthecloud247.com/wp-content/uploads/2020/03/Azure-AD-Conditional-Access01.png"
Named Locations
Countries location
Determined by the country's public IP address or GPS coordinates
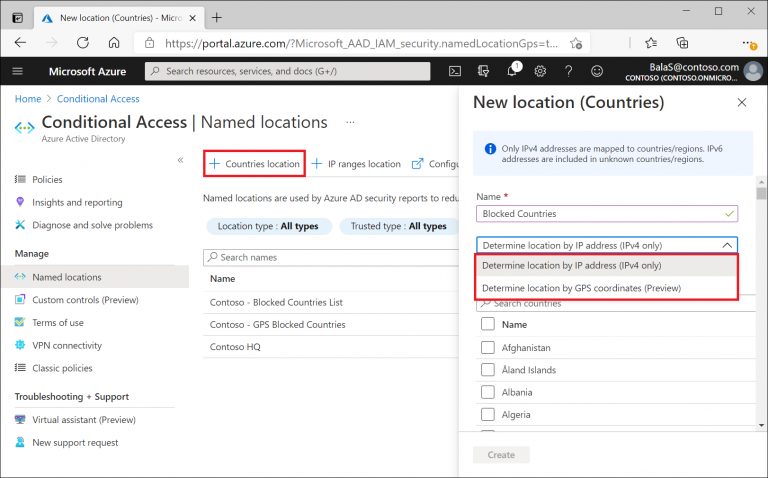
IP Ranges location
Determined by the customed defined IPv4/IPv6 ranges

Note: Mark as Trusted location helps to improve the accuracy of Azure AD's Identity Protection risk score, if the location is marked as trusted generally risk scores from these locations will be lower
Conditional Access Policy
In the policy configurations, there are several conditions could be configured based on the administrator's preference.
Assignments
1) Users and Groups; Selecting based on groups of users, directory roles or external guest users to apply this policy to and who are excluded from the policy.

2) Cloud apps or actions; Selecting which are the specific M365 applications that will be evaluated based on the policy and who are excluded from the policy

3) Conditions; Selecting access based on the device platform, locations, client apps (Installed on their endpoint) and state of their device.
Device platform; selecting the Operating system used by the user to apply the policy.

Location; selecting the defined location configured in the "Named Location" within the Azure AD (E.g. select all location to include and exclude the specific location to exclude from the policy)

Clients apps; selecting the list of client's apps to apply the policy

Device state; select the state of the device to apply the policy to e.g. if the device is Hybrid AzureAD joined or device is compliant or any state.

Access Controls
Grant; providing whether to block or grant access (with several selected conditions). Based on the list of condition, there are control options to select all selected condition must be match or any of the selected condition.

Session; To configure a custom limited experience within specified cloud applications.

Conditional Access allowed through Zscaler
There is use case where company would like to have their user's traffic to go through Zscaler, below are the configurations needed for such policy enforcement to take place. (This sample configuration compliments to the above sections where the below will focus on configuring to allow traffic from Zscaler's service edge node.)
Under Assignment --> Users and groups, on the tab "Include" select "All users" (Exclude any users under the "Exclude" tab)

Under Assignment --> Cloud apps or actions, on the tab "Include" select "All cloud apps" or if there are specific apps you would like to enforce only select "Select apps" and choose all app accordingly.

Under Assignment --> Conditions --> Device platforms, select the device platform you would like to be enforced if there are specific platform you would like to enforce you can go to "Include" and select the list of platform otherwise you can select "Any device"

Under Assignment --> Conditions --> Locations, (Since we would like to block all other location except for Zscaler's service node) we will need to select "Any location" under the "Include" tab)

Under the "Exclude" tab we will select the allowed location which in this case the trusted location we want Azure AD to accept connection from.

Since this is to block any other IPs from connecting to M365 however allow only Zscaler service edge IPs, we will configure the policy to block all IPs but allow Zscaler service node IPs.
Under Access controls --> Grant, select "Block access" to block all IPs from connecting (Excluding of Zscaler's service node IPs under name location have been configured on above steps)

Reference if Conditional Access policy is not met (Login from non-approved location)
_LI-medium.jpg)
For more information about Microsoft Conditional Access, please refer to:
Building Conditional Access Policy (https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/concept-conditional-access-policies)
Adding named locations (https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/location-condition)

